ZyLAB is proud to announce the achievement of SOC2 Type II certification today for both ZyLAB ONE and ZyLAB Legal Hold. The achievement of this key security certification is another major milestone in ZyLAB’s Security roadmap. It again emphasizes the importance ZyLAB places on the security of its solution, and reassures our customers that security is still a primary concern within ZyLAB.
ZyLAB has been operating in compliance to the SOC2 type II requirements for the past few years. This compliance has now been validated by a certified external organization. SOC2 type II ensures ZyLAB can securely manage customer data and is able to protect the interests and privacy of our customer’s organizations.
ZyLAB is active in the truth finding arena (eDiscovery), which requires ZyLAB not only to produce secure software, but also to operate a secure SaaS platform. Customers need a high level of security for their information being processed via ZyLAB, so both the software and the SaaS platform need to be secure in the broadest meaning of the word. To support ZyLAB’s mission and vision, the SOC2 service commitments are defined to include the full scope of the SOC2 framework: Security, Confidentiality, Availability, Processing Integrity and Privacy.

What exactly is SOC2?
SOC2 is one of the most sought-after standards in security and compliance. It represents the highest degree of excellence in systems and operations control. SOC stands for Service Organization Control, and was developed by the American Institute of CPAs (AICPA). SOC2 is specifically designed for service providers storing customer data in the cloud.
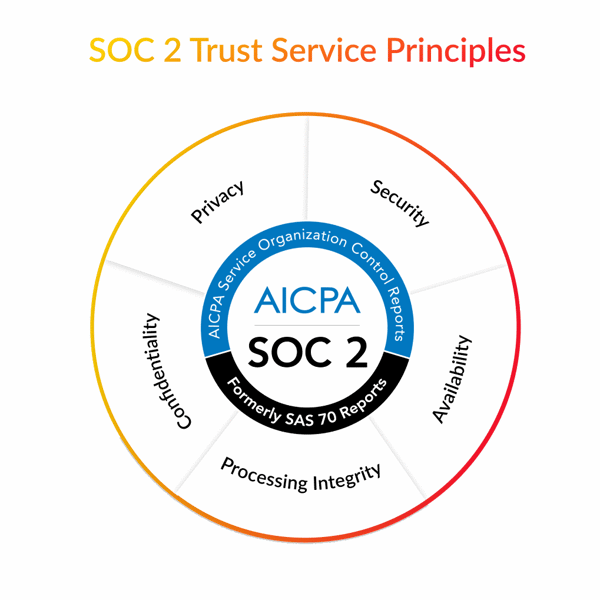
SOC2 requires companies to establish and enforce strict information security policies and procedures. The criteria for developing these policies and procedures is based on five “trust service principles”:
- Security – physical and logical protection against unauthorized access;
- Availability – system availability for operation and use as agreed upon;
- Confidentiality – information designed as confidential is protected as agreed upon;
- Processing Integrity – processing services are provided completely, accurately, and timely;
- Privacy – personal information is collected, used, retained, disclosed, and destroyed in accordance with the service organization’s privacy notice and business objectives.
The Security principle includes the so-called common criteria which are categorized as follows:
|
|
 The SOC2 type II Certification Process
The SOC2 type II Certification Process
SOC2 certification requires the adoption of policies and procedures for protecting information in areas including human resources, physical security, software development, operational security, business continuity, access management, asset management, vendor management, etc. To be certified, a company must evaluate all their people, processes, and IT systems and systematically apply risk management processes to each.
In order to examine ZyLAB’s security standards and operations, an external certified auditing entity was needed to ensure ZyLAB ONE and Legal Hold are compliant and follow best practices. For both SOC2 type I and SOC2 type II, we selected 2-Control as our auditors to achieve SOC2 certification.
With 2-Control, we have performed a thorough and detailed analysis of the existing security standards of ZyLAB, and worked tirelessly to meet the requirements of the SOC2 framework. The entire SOC2 criteria (Trust Service Principals) was scoped for the audit. Every criterion holds dozens of controls and measures, and each should be checked against security practices within ZyLAB. Simply maintaining security practices isn’t enough- you have to make sure that each security measure is well-documented and its performance is evaluated.
To analyze each control, and fine tune or extend our current security standards to meet the SOC2 certification requirements, ZyLAB established a cross functional team. Once completed, everything was verified by 2-Control during a 3 day audit which. The result of that audit is a detailed SOC2 report illustrating ZyLAB’s security standards, as well as a description of its systems and operations..
The components of a SOC 2 report include:
- Independent Service Auditor’s Report – containing a description of the service auditor’s examination of the suitability and effectiveness of the controls to meet the Trust Services Criteria.
- Assertion – containing a description for users of the service organization’s system controls, intended to meet Trust Services Criteria.
- System Overview – providing background information on the service organization of the software, people, procedures, and data within the organization’s environment.
- Relevant Aspects of Controls – providing a description on the control environment, the risk assessment process, information communication systems, and monitoring of controls.
- Trust Services Criteria, Related Controls, and Tests of Controls – outlining the controls in place and describing the tests on the effectiveness of the controls to meet the Trust Services Criteria.
- Other Information provided by the Service Organization
Why SOC2 matters for eDiscovery
Businesses and law firms use eDiscovery technology to manage massive amounts of data during critical legal and business-oriented processes. These processes include litigation, arbitration, responding to subpoenas and regulatory requests, monitoring compliance, preparing virtual data rooms, and so on. Government agencies use eDiscovery for many of the same reasons as well as to help prepare responses to public records requests.
The data involved in these processes almost always contains significant amounts of private and confidential information. Information which, if exposed to the public or obtained by hackers, could cause catastrophic financial and reputational damage, as described above. A SOC2 certification establishes that an eDiscovery vendor has taken every possible precaution to address any and all potential security risks to ensure customer data is constantly and consistently protected.
Your security matters to us
ZyLAB appreciates that customers place their trust in our company every day, and we believe we have a responsibility to manage and protect our customers’ information assets in exactly the same way as we protect our own.
The Management Team of ZyLAB takes this responsibility very seriously and is fully committed to comply with industry best practices in regards to information security, as shown by our overall Security strategy, and proven by our ISO27001 and SOC2 type II certifications, among others.
Since 2017, ZyLAB’s policies, procedures and way of working have been formalized according to the ISO/IEC 27000 series. In November 2018, ZyLAB obtained the certification proving that it has successfully implemented an information security management system (ISMS) in accordance with ISO/IEC 27001:2013. Now, ZyLAB has also gained certification according to the SOC2 framework controls, proving advanced implementation of security standards.
For more information visit our trust center


